Key points
-
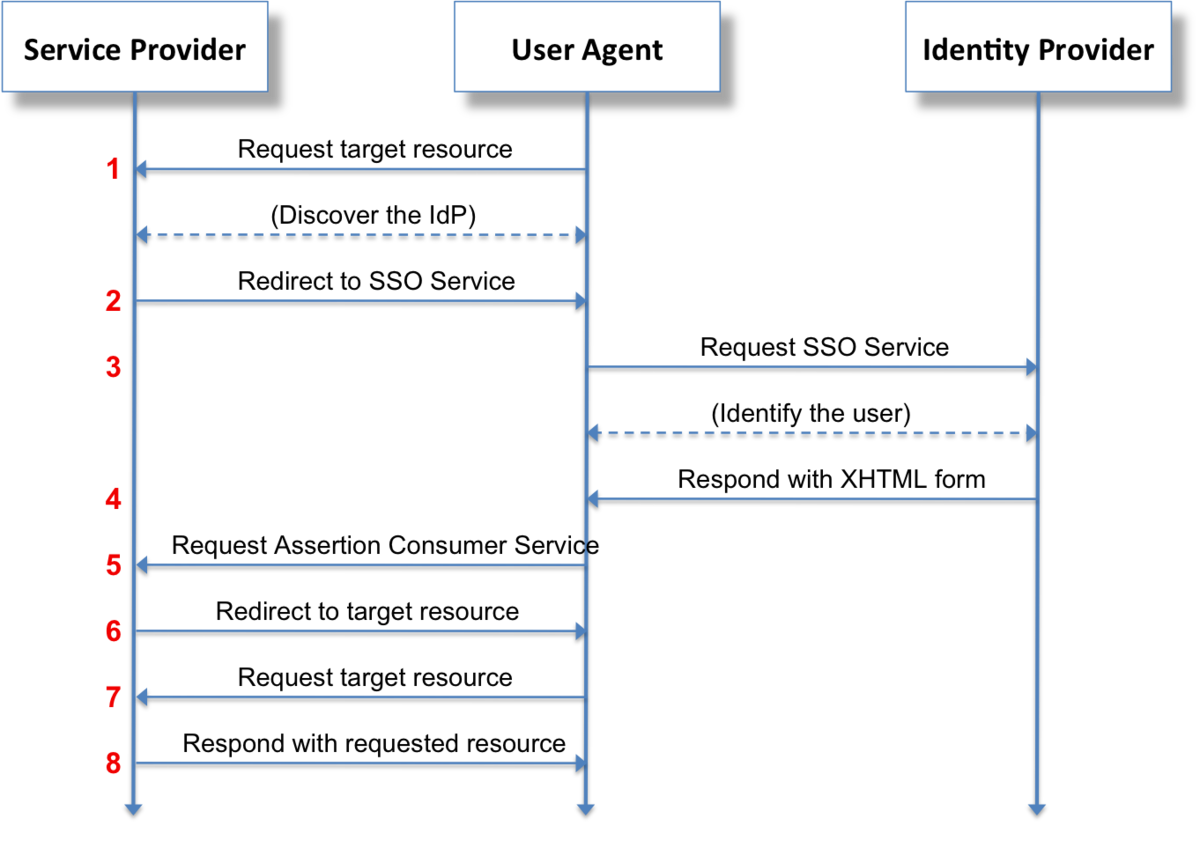
Mostly used as a web-based authentication mechanism because it relies on using the browser agent to broker the authentication flow.
-
The SP never directly interacts with the IdP. A browser acts as the agent to carry out all the redirects.
-
The SP needs to know which IdP to redirect to before it has any idea who the user is.
-
The SP doesn't know who the user is until the SAML assertion comes back from the IdP.
-
This flow doesn't have to start from the SP. An IdP can initiate an authentication flow.
-
The SAML authentication flow is asynchronous. The SP doesn't know if the IdP ever completes the entire flow. Because of this, the SP doesn't maintain any state of authentication requests generated. When the SP receives a response from an IdP, the response must contain all the necessary information.
Workflow
SAML 2.0
SAML Authority
SAML Identity Provider
e.g. Microsoft Entra ID
-
Issues
SAML assertions -
Defined by
IDPSSODescriptorin metadata schema -
Requires
SP's sign-in endpoint to whichSAML responsesare posted
SAML Relying Party / SAML Service Provider
-
Receive
SAML assertionsfromSAML Identity Provider -
Defined by
SPSSODescriptorin metadata schema -
The
SPneeds to obtain thepublic certificatefrom theIdPtovalidate the signature. The certificate is stored on the SP side and used whenever aSAML responsearrives. -
Requires
IdP's public certificate forsignature validationIdP's sign-in endpoint to whichSAML requestsare posted
Message Bindings
Different ways to send SAML messages between SP and IdP.
-
HTTP RedirectSAML protocol messages can be carried directly in the URL query string of an HTTP GET request. Since the length of URLs is limited in practice, the
HTTP Redirectbinding is suitable for short messages, such as the<samlp:AuthnRequest>message, and unsuitable for long messages, such as the SAML response message.The value of the
SAMLRequestparameter is thebase64-encodingof a<samlp:AuthnRequest>element, which is transmitted to theIdPvia thebrowser. -
HTTP POSTUsually for sending SAML response
-
HTTP ArtifactA SAML message is transmitted from one entity to another either
by valueorby reference. Areference to a SAML messageis called anartifact.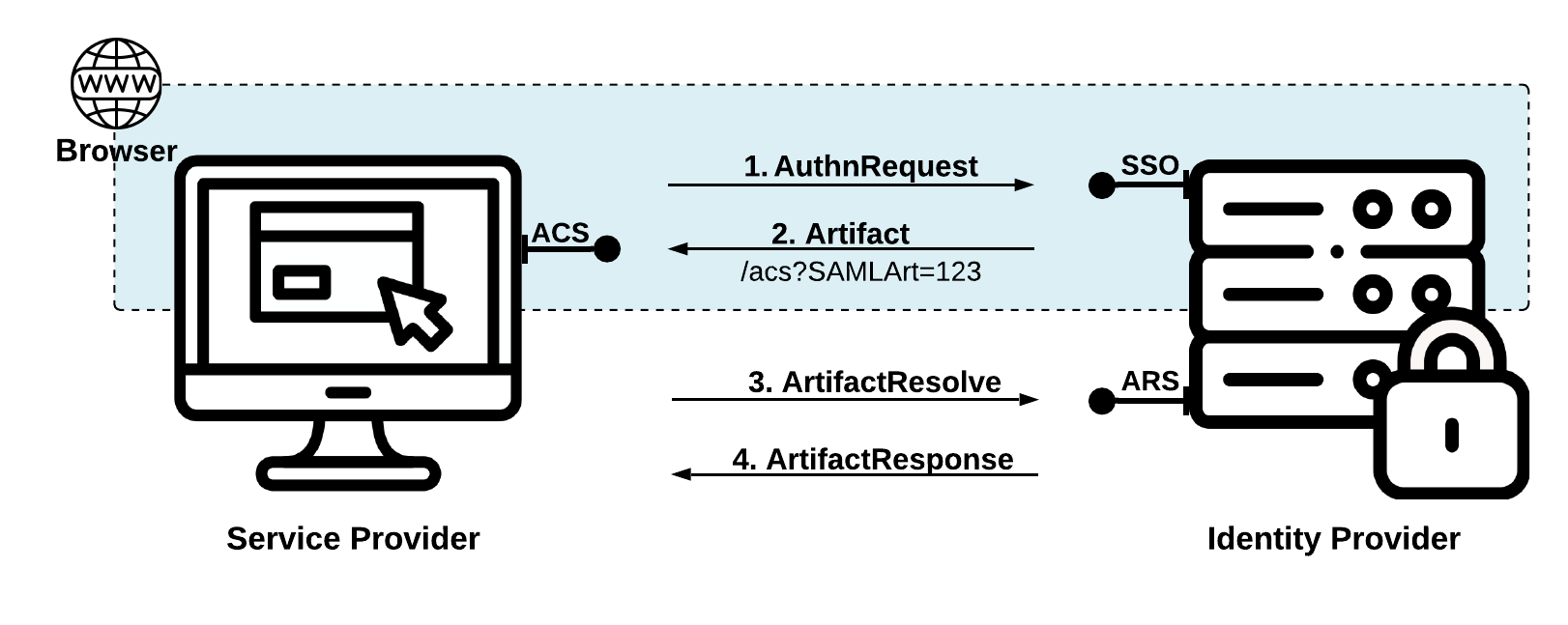
-
Resources
Example
IdP (Microsoft Entra ID)
-
Azure console
-
Home
-
Enterprise applications
-
<The application you have created>-
Manage
- Single sign-on
-
-
-
-
-
Basic
SAMLConfiguration (forSP)Microsoft Entra ID Spring Security SAML2 Example value Notes Identifier (Entity ID)Saml2RelyingPartyProperties.Registration.entityIdmicrosoft_entra_saml_toolkitSP's SAML2 Entity ID, must be unique across all applications in yourMicrosoft Entra tenant. The default identifier will be the audience of theSAML responseforIdP-initiated SSO.Reply URL (Assertion Consumer Service URL)Saml2RelyingPartyProperties.Registration.acshttp://localhost:8444/SAML/ConsumeSP's ACS endpoint, where the application expects to receive theauthentication token, akaAssertion Consumer Service (ACS)inSAML.Sign on URLhttps://samltoolkit.azurewebsites.net/saml/loginSP's sign-in page URLforSP-initiated SSO, unnecessary if you want to performIdP-initiated SSO.Relay State (Optional)<Optional>SP's endpoint for a successful authentication, to whichusers are redirected after authentication is completed, and the value is typically a URL or URL path that takes users to a specific location within the application.Logout URL (Optional)<Optional>SP's endpoint for a successful logout, to which the SAML logout response (saml2p:LogoutResponse) is sent.
SP (Spring Security - SAML2)
-
org.springframework.security.config.annotation.web.configurers.saml2.Saml2LoginConfigurer -
org.springframework.boot.autoconfigure.security.saml2.Saml2RelyingPartyPropertiesSAML2 relying partyproperties -
org.springframework.boot.autoconfigure.security.saml2.Saml2RelyingPartyRegistrationConfiguration@Configurationused to mapSaml2RelyingPartyPropertiesto relying party registrations in aRelyingPartyRegistrationRepository. -
org.springframework.security.saml2.provider.service.web.Saml2WebSsoAuthenticationRequestFilter -
application.yamlspring: security: saml2: relyingparty: registration: app-name: entity-id: "microsoft_entra_saml_toolkit" # SP's SAML2 Entity ID singlelogout: binding: POST # Whether to redirect or post logout requests. url: "{baseUrl}/saml/logout" # Location where SAML2 LogoutRequest gets sent to responseUrl: "{baseUrl}/saml/SingleLogout" # Location where SAML2 LogoutResponse gets sent to, Microsoft Entra ID (Basic SAML Configuration - Logout Url (Optional)) acs: location: "{baseUrl}/saml/consume" # Microsoft Entra ID (Basic SAML Configuration - Reply URL (Assertion Consumer Service URL)) assertingparty: # IdP details (In this case, Microsoft Entra ID), if metadata URL is used, no need to configure other properties metadata-uri: https://login.microsoftonline.com/4e85adc7-d172-460b-8494-c13fe4e9e43e/federationmetadata/2007-06/federationmetadata.xml?appid=81e5c415-19cf-45fe-b923-9e99f7955f82 # Microsoft Entra ID (SAML Certificates - App Federation Metadata Url) -
Filters
Name Notes Type Saml2WebSsoAuthenticationRequestFilterFormulates a SAML 2.0 AuthnRequestorg.springframework.security.saml2.provider.service.web.Saml2WebSsoAuthenticationRequestFilterSaml2WebSsoAuthenticationFilterAttempts to perform authentication from SAML 2.0 Response; UseAuthenticationConverterto convertSAML 2.0 ResponsetoAuthenticationtokenorg.springframework.security.saml2.provider.service.web.authentication.Saml2WebSsoAuthenticationFilter
Tools
- SAML DEVELOPER TOOLS (opens in a new tab)
- Mock SAML - A free SAML 2.0 Identity Provider for testing SAML SSO integrations. (opens in a new tab)
Troubleshooting
Signature Validation Error
This could be caused by spaces in the certificate Base64-encoded string. Use a one-line string to represent the certificate.
Resources
-
Reference
-
Troubleshooting